
CIS v8 made simple
Complyance makes CIS v8 implementation practical for IT and security teams. AI reviews evidence and issues reminders to keep controls current, while deep configurability and hands-on support ensure a smooth rollout and sustained compliance.

































Ready-to-use CIS v8 mappings reduce setup and configuration time.

AI features track control status and send reminders to keep CIS v8 evidence current between audits.

Fit CIS v8 implementation to your IT and security environment.

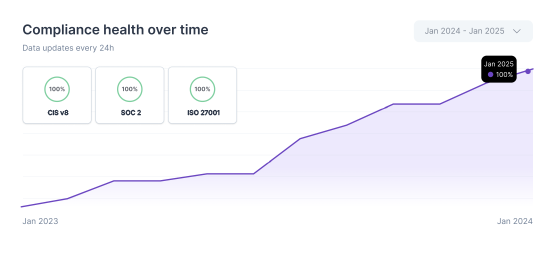
CIS v8 evidence can be cross-mapped with NIST, ISO, and SOC frameworks for unified oversight.
CIS v8 automation
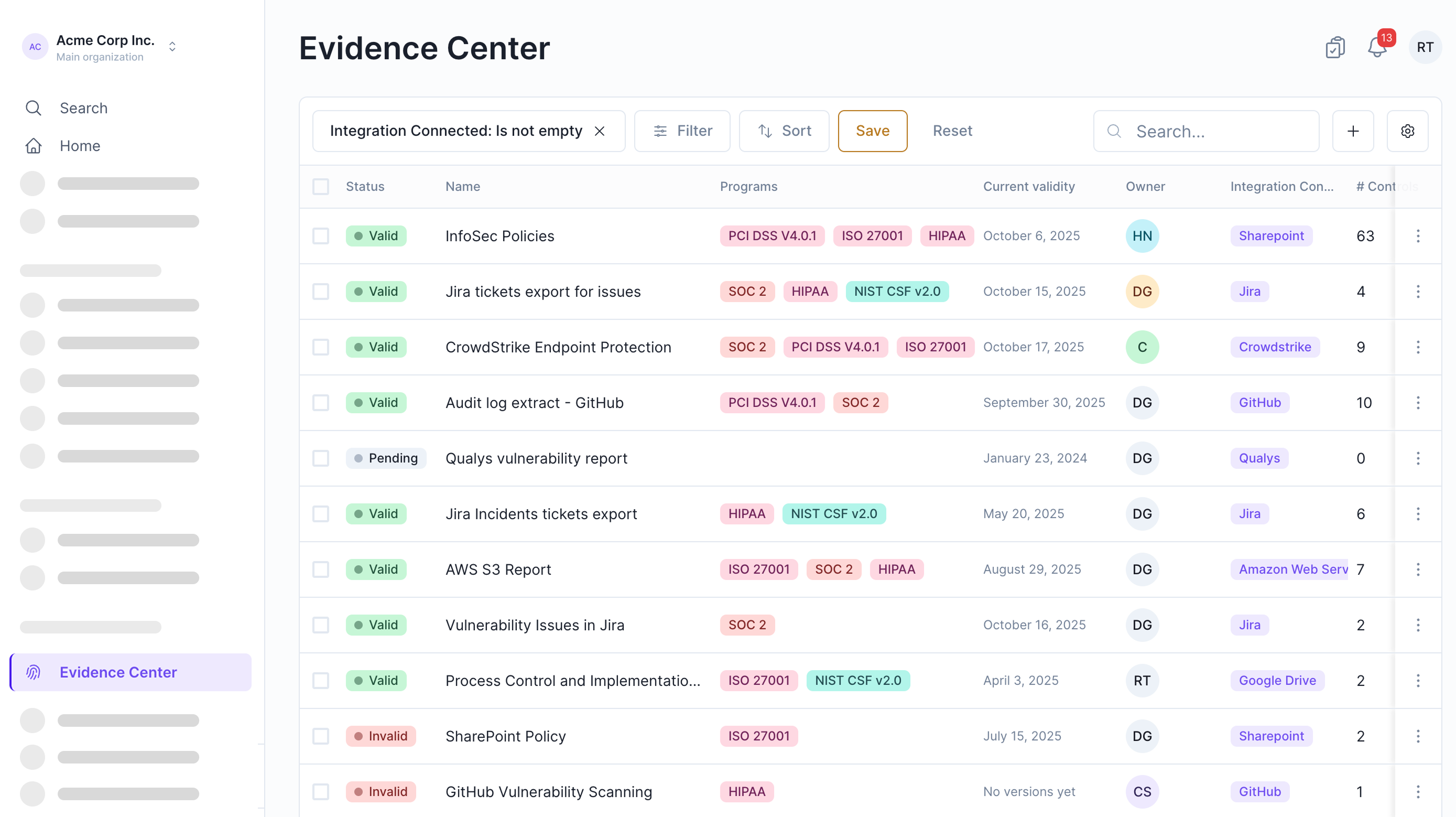
Automate CIS v8 evidence collection
Complyance automates evidence updates and reviews with AI support, helping teams maintain readiness with less manual work.
CIS security framework
Configurable controls and tracking
Adapt CIS v8 implementation to your IT and security processes through flexible, configurable workflows.
Unlimited control owners
Deploy CIS v8 across teams and departments without per-user limitations.
Related resources
Read more on this topic
Frequently asked questions
The Center for Internet Security v8 defines critical security controls to protect IT systems and sensitive data.
Enterprises, government agencies, and vendors looking to strengthen their cybersecurity baselines.
Complyance connects systems to keep evidence linked and uses AI to review controls, trigger reminders, and support continuous monitoring.
Yes. CIS v8 controls can be cross-mapped with ISO, SOC, NIST, and HIPAA frameworks for unified compliance.
Complyance combines automation, AI insights, configurability, and expert support to simplify and accelerate CIS v8 adoption.





